Grayshift has gone to great lengths to future-proof their technology and stated that they have already defeated this security feature in the beta build. Grayshift has made strides to future proof its technology and revealed USB Restricted Mode in iOS 12 Bypassed by Grayshift.

USB Restricted Mode in iOS 12 Bypassed by Grayshit – Cops Are Confident
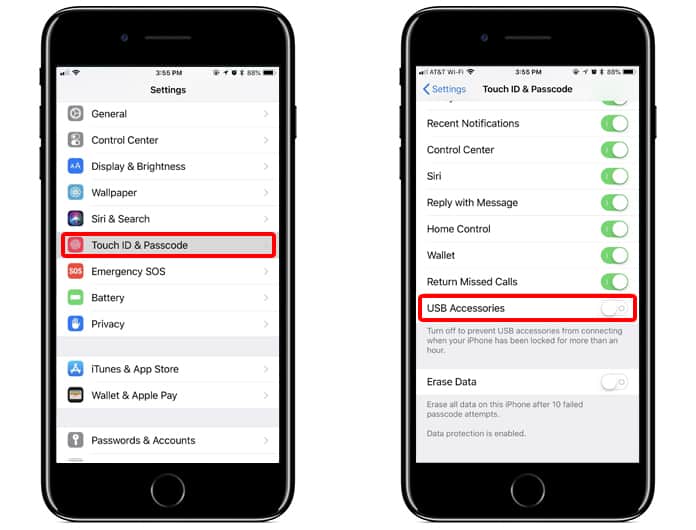
Last week, Apple said it was going to launch a new security feature called USB Restricted Mode. It basically converts the lightning cable port of the iPhone into a charge-only interface if the device hasn’t been locked with a passcode in the last hour, implying forensic tools shouldn’t be able to unlock the device.
As expected, the introduction sent waves throughout the law enforcement and phone forensic community, as accessing the device might now be significantly difficult. Also, investigators will have to be quick with converting a seized smartphone to an unlocking one. That compromises of GrayKey, a new yet popular cracking tool for iPhone. Leading forensic companies state that the firm behind the technology hasn’t given up yet.
According to an email from a forensic specialist who was supposed to have a meeting with Grayshift, Grayshit has made a big effort to future proof its technology and stated that it has already defeated the security feature of the beta built. Moreover, the GrayKey is integrated with capabilities that will be utilized as time goes on. The email adds that Grayshift is confident of staying relevant in the future.

A second individual, replying to the email, stated that the USB Restricted Mode was addressed by Grayshift in a webinar several weeks ago. However, the new feature is still alarming Apple.
The tipper of the story – Motherboard – also revealed that Grayshift has formed relationships with local, state, and federal law enforcement agencies, including the Secret Service, DEA, and FBA. Some emails also revealed that Grayshift is in contact with the New York State Police.
As for the GrayKey, it is a tiny box that includes lighting cables for forming a connection between two iPhones simultaneously. Although the technical information on how the phone is infiltrated by GrayKey is unavailable, the device, surprisingly, relies on techniques for churning through different combinations of passcode, or brute forcing.

According to Grayshift’s slides, the device has two methods of accessing data on the smartphone – Before First Unlock “BFU” and After First Unlock “AFU.” BFU relies on slow brute force, implying 10 minutes are needed per attempt. The user gets access to limited data because BFU strategy occurs when the device is off when seized. If the case is that, when switched off, the iPhone’s data is still encrypted.
In contrast, AFU is a “fast brute force” mode that functions when the device is locked but is switched on and has been unlocked by the owner at some point. In this scenario, 300,000 attempts are allowed and pre-unlock data’s parallel extraction is enabled. If AFU functions, 95 percent of the data is instantly made available. The slides were displayed in a GrayKey presentation at a mobile forensics event in South Carolina.
But the USB Restricted Mode has placed severe restrictions on this form of attack, because the lighting port utilized for attacking the smartphone becomes useless after an hour has passed without unlocking the device. As reported by Motherboard earlier in the month, the feature becomes available in iOS 12 beta, the upcoming OS by Apple. It hasn’t been introduced in general iOS releases, but expect iOS 12 to launch around June 12. In iOS beta, USB Restricted Mode is switched on by default but can be deactivated.
Apple revealed in a statement offered to the New York Times and Reuters that they put the customer at the center stage of everything they design, and they’re working hard to secure every Apple product so that customers can defend against identifying thieves, hackers and adversaries. Also, the company has a lot of respect for law enforcement agencies, and doesn’t design its items to frustrate their efforts.
Maryland State Police has access to the GrayKey technology. Elena Russo, agency spokesperson, told Motherboard that the MSP (Maryland State Police) Digital Forensics Lab has a range of software and hardware tools to carry out criminal investigations, that include the Grayshift product. And they plan to continue using these tools for producing the best outcomes.
Indiana State Police’s chief public information officer David R. Bursten has also purchased GrayKey. He told motherboard that the technology continues to evolve and law enforcement is trying its best to respond on a continuous basis.
No comment came from Grayshift.


![How to Disable Keyboard Click Sounds on iPhone/iPad [Tutorial] disable keyboard click sounds on iphone](https://cdn.unlockboot.com/wp-content/uploads/2019/03/disable-iphone-keyboard-sounds-324x160.jpg)






![30 Best Cydia Repo Sources For iOS 16/15/14 Jailbreak [2024] best cydia sources 2020](https://cdn.unlockboot.com/wp-content/uploads/2020/06/cydia-sources-13-100x70.jpg)